The cybersecurity industry scrambled to deal with the latest social media based threat after a user profile named ‘TomLiner’, the same profile associated with a similar leak involving Facebook, carried out a massive data scraping exercise that compiled and leaked LinkedIn profile data of around 700 million users into a database published earlier this week.
In local terms, this means that up to 202,500 users in Malta may have been affected, according to the information available on local LinkedIn users as compiled by NapoleonCat, a social media management firm. A similar Facebook leak in April had targeted more than 100,000 local users.
‘Data scraping’ is a technique that exploits the code that powers websites like Facebook and LinkedIn by using it to comb through hundreds of millions of profiles, gathering information such as a user’s name, online ID, profile URL, location and email address, irrespective of whether a user sets their privacy settings to conceal information from the public or not. Scraping differs from an actual data breach because a breach means that safety features such as password access have been circumvented.
The hacker profile, TomLiner, published the data earlier this week after attempting to sell it on hacker forums in June. At the time, LinkedIn issued a post specifically outlining that the data was scraped and that none of its internal security measures was actually breached.
When reports of the massive data dump being published this week started circulating, LinkedIn has since then redirected reporters’ questions to its previous statement made earlier in the year. Several prominent tech sites have reported obtaining a copy of the database and have verified its authenticity.
Overall, the past two years have seen a significant increase in cybercrime, in terms of scale, sophistication and severity of threats. The US Federal Bureau of Investigation, in its annual Internet Crime Report, outlined how it collected 791,790 complaints of suspected online crime in 2020, amounting to $4.2 billion in losses as a result in the US alone. The FBI received 467,361 complaints in 2019.
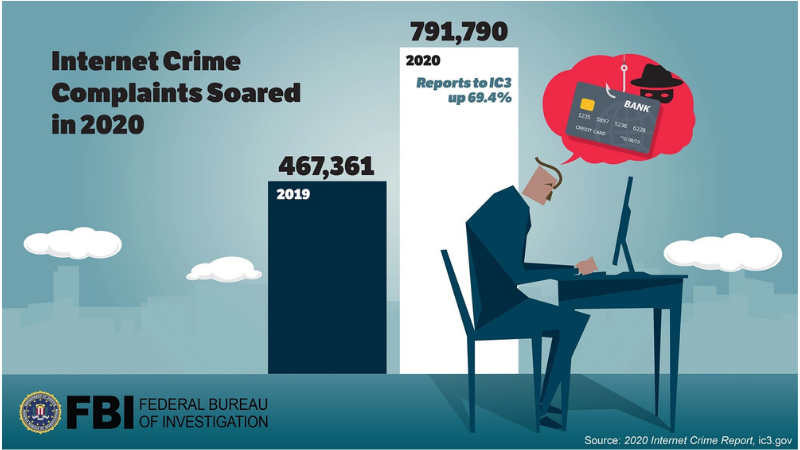
A graphic published by the FBI on increase in cybercrime complaints
The LinkedIn leak, amounting to approximately 187GB of data that is currently being shared around on the messaging app known as Telegram, is one of an increasing number of such data sets being sold and shared across the world.
While the average social media user might not see the value in a database that was scraped from largely publicly available information that users willingly shared, a hacker seeking to coordinate scams and phishing attacks could easily collect various data sets from leaks such as the ones that sourced data from LinkedIn and Facebook and build an accurate, informed understanding of that person’s identity.
For example, a scammer seeking to target or impersonate an employee with access to sensitive company information or even access to bank accounts would be able to collate information from different databases about the same set of targets, thus being able to write convincing emails impersonating others or generally direct behaviour towards the hacker’s goals.
Analytics Insight reported how Socialarks, a Chinese social media management firm, was subjected to an actual breach of internal security, with hackers gaining access to around 400GB of personal information of at least 214 million people. The stolen data included mobile numbers, accounts and logins, pictures and even insights into targeted users’ audiences.
A hacker could combine data from the Socialarks and LinkedIn leaks should their target happen to be using both platforms.
You can read more about what you can do to secure your digital footprint here and here.














